RASP security and traditional application security both come with their own sets of advantages and drawbacks, which is why to select the appropriate option for your business you should understand their differences. RASP security provides cutting-edge safeguards that offer comprehensive coverage against online application threats while being user-friendly; traditional approaches tend to be complex and complicated to maintain over time.
Conventional Application Security Has Its Own Set Of Advantages And Disadvantages
Stability is one of the greatest assets of any application when it comes to security. Proven models have been rigorously evaluated over time and proved their worth; furthermore, these deployment and administration models are easy for anyone familiar with them to deploy and administer them effectively. Perimeter security solutions that have been around longer providing great protection from outside intrusion attempts.
But there are several flaws with how applications have historically been secured. Safety measures may not always be straightforward to implement and maintain. Signature-based threat identification solutions often rely on signature-matching approaches; however, these cannot detect zero-day assaults. Furthermore, traditional solutions lack visibility into application activity which makes identifying attacks harder.
RASP Security: What It Is | An Analysis of Protecting Applications From Cyberattacks in Real-Time
Every company that runs operations on software must put application security at the forefront. A breach could have serious repercussions for their operations as well as reputational harm and customer trust issues; as a result, any such company needs to understand different forms of application security and how they function.
RASP security (Real-Time Application Security Protection) is a relatively novel form of application protection with many advantages over more traditional approaches. We will explore RASP in more depth here and see how it can protect your apps.
How Does RASP Protection Function?
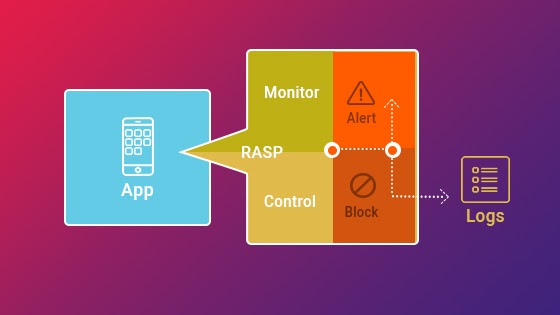
RASP security can add an extra layer of protection for applications using RASP security, giving them the capability of monitoring user activity and detecting any malicious behaviours immediately. Furthermore, RASP can protect against various attacks including exploiting vulnerabilities within the application code itself.
RASP security is effective because it monitors application data flows and flags any irregularities, enabling RASP security to block malicious requests before they reach its applications and protect against known and unknown attacks by identifying suspicious behaviour and blocking suspicious behaviour.
RASP security can protect against various attacks, including those that exploit vulnerabilities in application code. It does this by detecting and blocking any suspicious requests before they reach the application and by protecting from known and unknown attacks by identifying and blocking suspicious behaviour.
Comparing Traditional Application Security and RASP Security: Key Differences and Similarities
Traditional application security differs significantly from RASP security in several key aspects, with RASP designed to thwart attacks that exploit vulnerabilities while traditional app security aims only at protecting applications against known attacks.
One key difference between RASP security and traditional application security products is their deployment model: RASP is typically deployed as a service while traditional security products typically need to be updated whenever new threats emerge whereas RASP updates immediately, while new versions of its product typically only do so at specific intervals.
RASP security can often be much simpler to deploy and configure than traditional application security due to its self-protecting nature; thus requiring less expertise for setup.
Though traditional application security and RASP security differ significantly, they do share similarities. Both aim to defend applications against attacks and can be deployed either as services or products.
Decisions between traditional application security and RASP security depend on the needs of an organization, particularly its level of protection required. If this requires maximum protection, RASP is often the superior option; otherwise, traditional application security might provide sufficient coverage or deployment and configuration issues may necessitate easier alternatives such as traditional IDS.
How RASP Security Works: Dynamic Analysis, Monitoring and Response?
RASP security is a form of web application security designed to shield web applications from attack. While traditional web app security relies on static analysis of application code, RASP uses dynamic analysis techniques that monitor application activity and detect potential threats immediately – offering more comprehensive protection from web attacks by responding to them immediately as they arise.
RASP security works by installing a security agent on the web server and monitoring all incoming traffic and activity for signs of an attack. Should such an attempt be detected, this agent will take immediate steps to block and notify administrators about it.
RASP security may be a relatively new technology, but it has already proven its worth in protecting web applications against attack. One study showed RASP blocking 100% of attacks compared to traditional web application security solutions which only blocked 60%.
RASP security can bring many advantages, such as:
Improved Security: RASP security offers a comprehensive defence against web attacks.
Reduced False Positives: Because RASP security relies on dynamic analysis, it is less likely to generate false positives than traditional web application security solutions.
RASP security provides a proven method of safeguarding web applications from potential attacks. If you require a more comprehensive defence against web-borne threats, RASP could be an excellent solution to consider.
Advantages of RASP Security: Faster Response Times, Reduced False Positives, and Expanded Capabilities
RASP (Runtime Application Self-Protection) has emerged as one of the most significant shifts in application security over recent years. RASP is an innovative new security solution that seeks to protect applications during runtime rather than using traditional measures applied during development or testing phases.
RASP security can offer many advantages over traditional solutions, including faster response times and reduced false positives.
RASP security’s most notable advantage lies in its fast response times, thanks to solutions designed for real-time monitoring and protection rather than periodic scans or manual reviews. RASP solutions allow immediate detection and response to security threats rather than waiting until the next scheduled scan.
RASP Security Can Reduce False Positives
Another benefit of RASP security is its ability to help reduce false positives. Traditional security solutions often encounter problems with false positives where seemingly benign activity is misidentified as malicious, leading to wasted time and resources from teams investigating these nonexistent threats. RASP security provides an innovative solution by eliminating false positives which can cut down on these costly false positives altogether.
RASP solutions can assist in minimizing false positives by providing more context about any activity being flagged, which enables more accurate detection of which activity is malicious and which is not. As a result, teams can focus their time and attention on real threats instead of spending too much time worrying about false positives.
Conclusion
Traditional application security focuses on recognizing and preventing attacks against an application itself; RASP security takes a different approach by safeguarding data processing and storage systems used by applications to process or store their data. While traditional security measures with Appsealing may help protect an app itself, RASP measures can protect their respective processes as well. Overall though, traditional measures tend to provide more comprehensive protection from attacks against applications themselves.